As you know there are different software that allow to encrypt users area.
Our developers proceed to research a ways for decrypt drives encrypted by software methods.
PC-3000 version 6.2.x allow to work with such encrypted drives and decrypt by special option in Data Extractor tool.
How to do it? – Welcome to this article!
In this video you can see the process of unlocking encrypted drive by BitLocker, but procedure is the same for all other supported encryption methods:
Please note that we are not break an encryption by something brute-force methods and not hack the encryption. Utility simulate a decryption process like it performed in original utility.
That’s why need to know an original key or have a key-file that encryption utilities create when user switch on the encryption option in the software.
At this time (PC-3000 version 6.2.x) we can work with partitions are encrypted by Windows Bitlocker, Apple FileVault and TrueCrypt.
When this option can be usefull?
For example drive can’t be recognized by OS because have damaged/problem head, then you can decrypt all available users data (via alive heads) without heads swap procedure.
Another example:
Drive have a problem with the files allocation tables and as result impossible to open the Root and files structure in OS, then you can use decrypt option in Data Extractor and analyse the partition – use a Scan INDX + MFT option or RAW recovery.
The procedure is following:
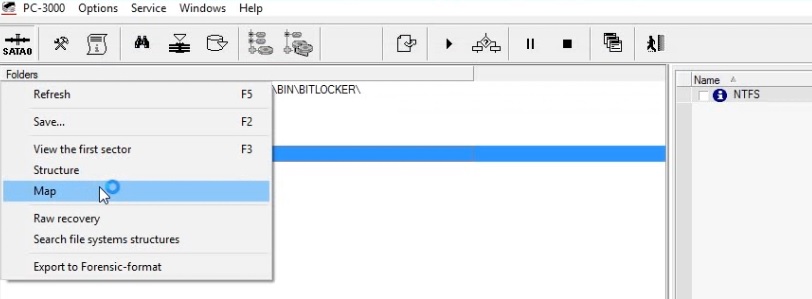
Create a new task in Data extractor software and build a map of encrypted partition.
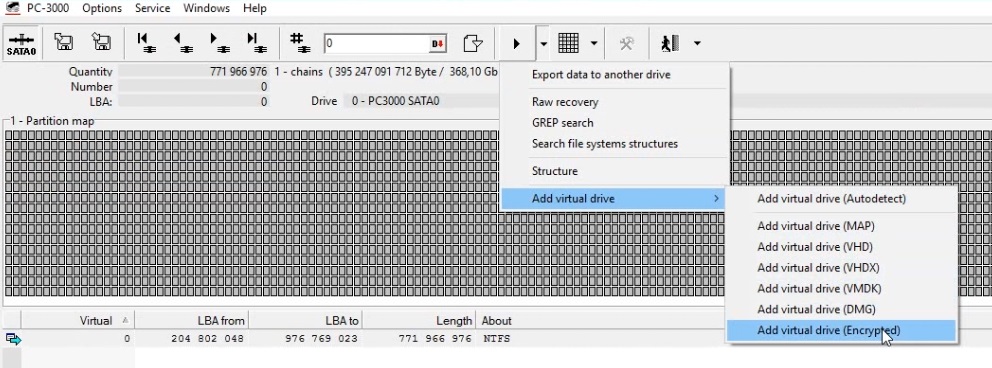
Add a Virtual drive. Use “Add virtual drive (Encrypted)” option.
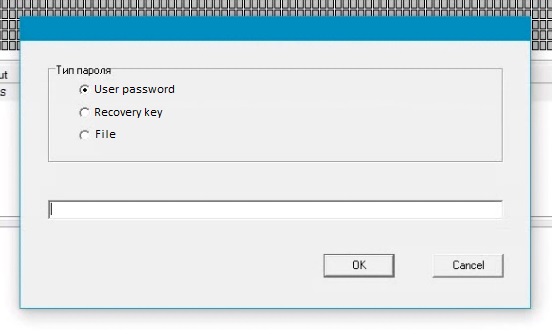
You will see the pop-up window that require to enter a password. Also you can use a Recovery key or load a password from file. These two option allow to decrypt a partition by special file that is also created when encryption option is launched in encryption tool.
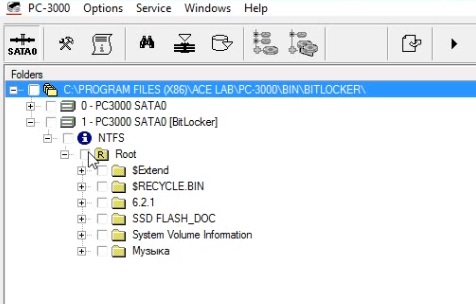
As result in Data Extractor will be created new virtual partition with decrypted users area.
As you can see all data are decrypted and available.
If you have something problems with this procededure – please contact us!




 (5 votes, average: 4.20 out of 5)
(5 votes, average: 4.20 out of 5)
Very nice
Does this address core storage?
Core Storage is way of volume managment on Apple devices. It can manage one or several volumes. CS with one volume usually called FileVault, CS with several volumes usually called Fusion drive. Standard Data Extractor supports FileVault with 512 and 4096 sector size. Data Extractor RAID supports Fusion drive with HFS+ and APFS file systems.
Thank you very much!
if i don’t have any password? 🙁 the customers forgot all ID and password
With out original password PC-3000 can’t expand a partition.
As wrote in this article:
“we are not break an encryption by something brute-force methods and not hack the encryption. Utility simulate a decryption process like it performed in original utility.
That’s why need to know an original key or have a key-file that encryption utilities create when user switch on the encryption option in the software.”
Hi, I have a case now with Bitlocker, the customer gave me keys to try and it may work out fine.
How about in forensics, we need a tool that can retrieve data without keys. I understand and respect your take on hacking and ethics, but this is an important requirement.
I was working in IT Security before and there is a subject called ‘ethical hacking’ that we were looking into. There were employees at a bank who encrypted disks and then left the company. They said that they did not remember the keys, but the bank was in real trouble. I believe that we should be able to help them – hacking or any other way that you can come up with.
Do not forget that many of the disks that we recover for companies have very sensitive information on them and this is not regarded to be a problem; why is breaking encryption a problem?
Think about it and see if you can come up with a win-win solution.
Hello. Such questions better to ask directly to TS department. We are not providing full recovery steps for customer problems in article comments.
Sir If WE Dont Know The Drive Password
Then How to Encrypt or recover Our Data ??
Please read article and comments again.
With out original password PC-3000 can’t expand a partition.
As wrote in this article:
“we are not break an encryption by something brute-force methods and not hack the encryption. Utility simulate a decryption process like it performed in original utility.
That’s why need to know an original key or have a key-file that encryption utilities create when user switch on the encryption option in the software.”
does the export feature just save a copy of the file on non damaged disks? Or will it use the hardware imager so we can image files and use the features of it? We are struggling with the ability of not being able to image the files since their is file damage on the drive – it doesn’t even put the files in the !Problem folder when saving… When you create a map and folder of the selected data we want to image – after its built – only option is to save it??? Why give us the map files and folder option when you cant use it – very confusing…
Dear Joseph,
When you decrypt BitLocker or Filevault partition Data Extractor creates a new virtual volume using encryption keys. So next actions you do with virtual volumes. Virtual volumes have some restrictions with map operations, for example you cannot re-read bad sectors of file using its map.
One possible solution to re-read bad sectors is to build submap of either entire volume or specific file based on drive info. This submap provides full functionality for operations with map. You can use multipass reading on this submap. After that, you can return to original virtual map and save file with improved sector content.